好像好久好久没更新博客了,水一篇WP好了
排名4
AK了逆向 多亏了@woodwhale教我lua,不然歇逼了
题目没啥难度,就是老喜欢自己写算法挺恶心人的。
pyccc
pycdc直接出代码,异或脚本即可
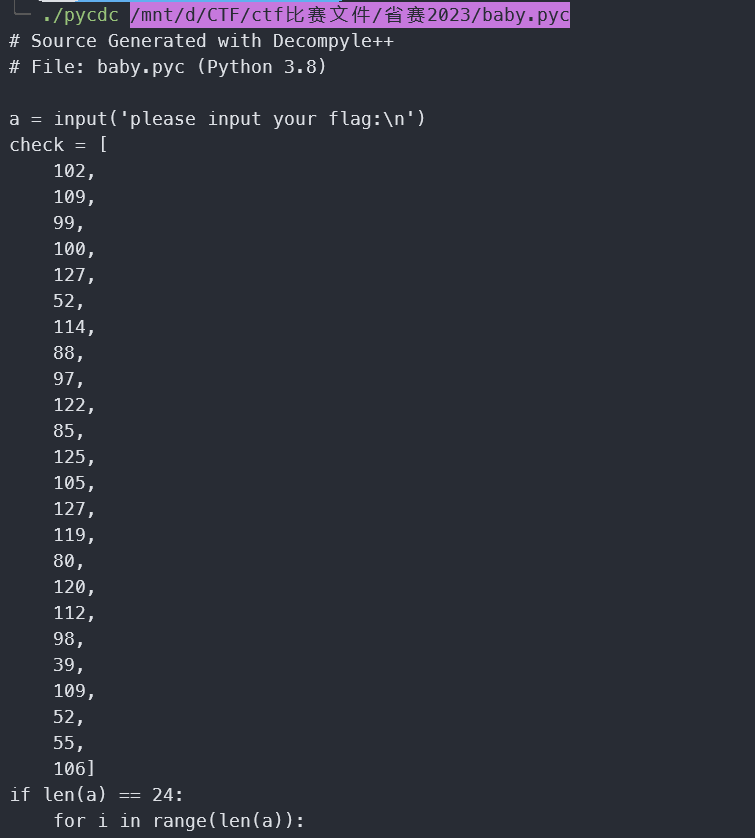
check = [
102,
109,
99,
100,
127,
52,
114,
88,
97,
122,
85,
125,
105,
127,
119,
80,
120,
112,
98,
39,
109,
52,
55,
106]
for i in range(len(check)):
print(chr(check[i] ^ i),end='')
luare
断点到000055C07F31848C可以搜内存搜到\x1bLua,dump出来binary形式的lua脚本
用unluac即可反编译出来,可以看到调用了Oo00Oo0
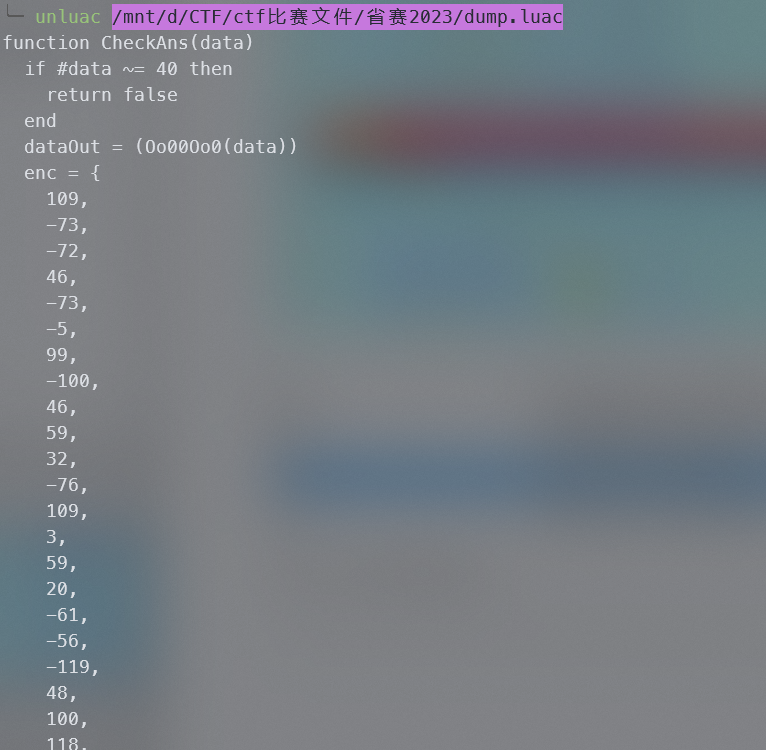
Oo00Oo0是一个取表替换的算法,写脚本解密即可
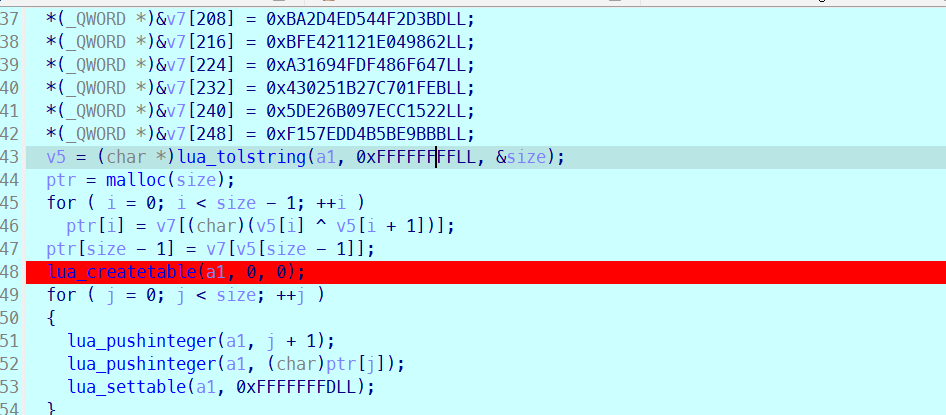
lines = '''0x60856D1028C8953C
0x964849764CB30359
0x2E7164C479B75FB8
0x80637291A7AC8C38
0x7B8BF3AE4B339EB0
0xCFE06FEC52B45B4D
0x5DC67EAAB20C3AD
0x24FCFBD656409F00
0x4AF00D463D0BCA92
0x7DBC8A3B1A11555A
0x3061CE7513A9E76C
0x9C54D007276AA614
0x34C20158D8898E5C
0x50A02AC02F3569E8
0xC0E681D39FF8836
0xB66E7F18FEB1E693
0x29F5D2E92B315378
0x41D9DBDE84172C0F
0x7A45A899A1F71906
0xE5AA0AAF1BA5233E
0x9A3A82FAF8E1A4EF
0xC1D173C7651C8FDF
0x8D9DDD875EA2D7C5
0x66EE9790CD81C9F9
0x370874C63F424FDA
0xB93283E32677CB25
0xBA2D4ED544F2D3BD
0xBFE421121E049862
0xA31694FDF486F647
0x430251B27C701FEB
0x5DE26B097ECC1522
0xF157EDD4B5BE9BBB'''
from pwn import *
global_data = []
def pares(data):
x = p64(int(data.strip(), 16))
global_data.extend(list(x))
for l in lines.splitlines():
pares(l.strip())
print(global_data)
res = [ 109,
-73,
-72,
46,
-73,
-5,
99,
-100,
46,
59,
32,
-76,
109,
3,
59,
20,
-61,
-56,
-119,
48,
100,
118,
36,
118,
82,
3,
95,
106,
14,
-80,
5,
-89,
89,
-85,
5,
14,
46,
-73,
7,
127]
flag = ''
from ctypes import c_uint8
last = global_data.index(res[-1])
flag += chr(last)
for i in range(39):
x = -i - 2
last = c_uint8(c_uint8(global_data.index(c_uint8(res[x]).value)).value ^ last).value
flag += chr(last)
flag = flag[::-1]
print(flag)easyapk
DES的名,AES的心,main替换了一下key的字符
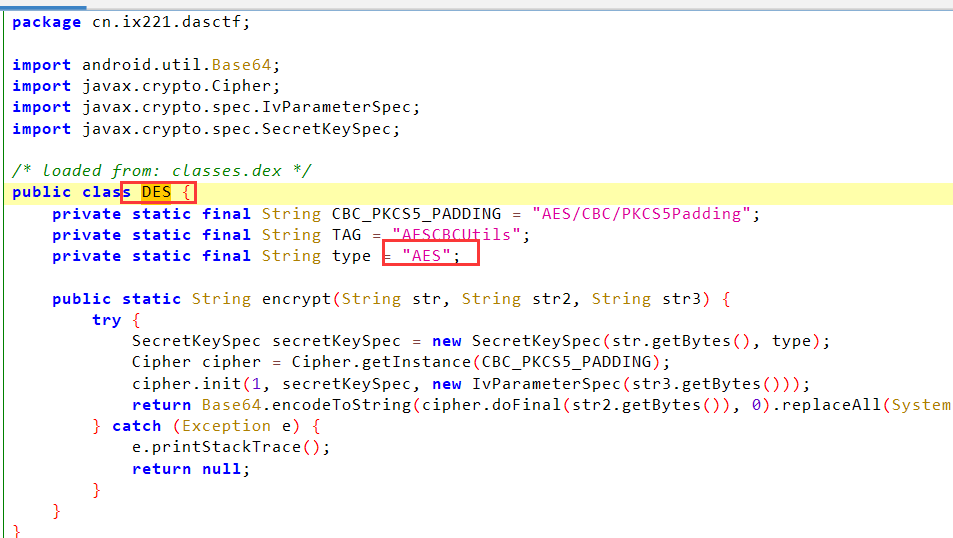
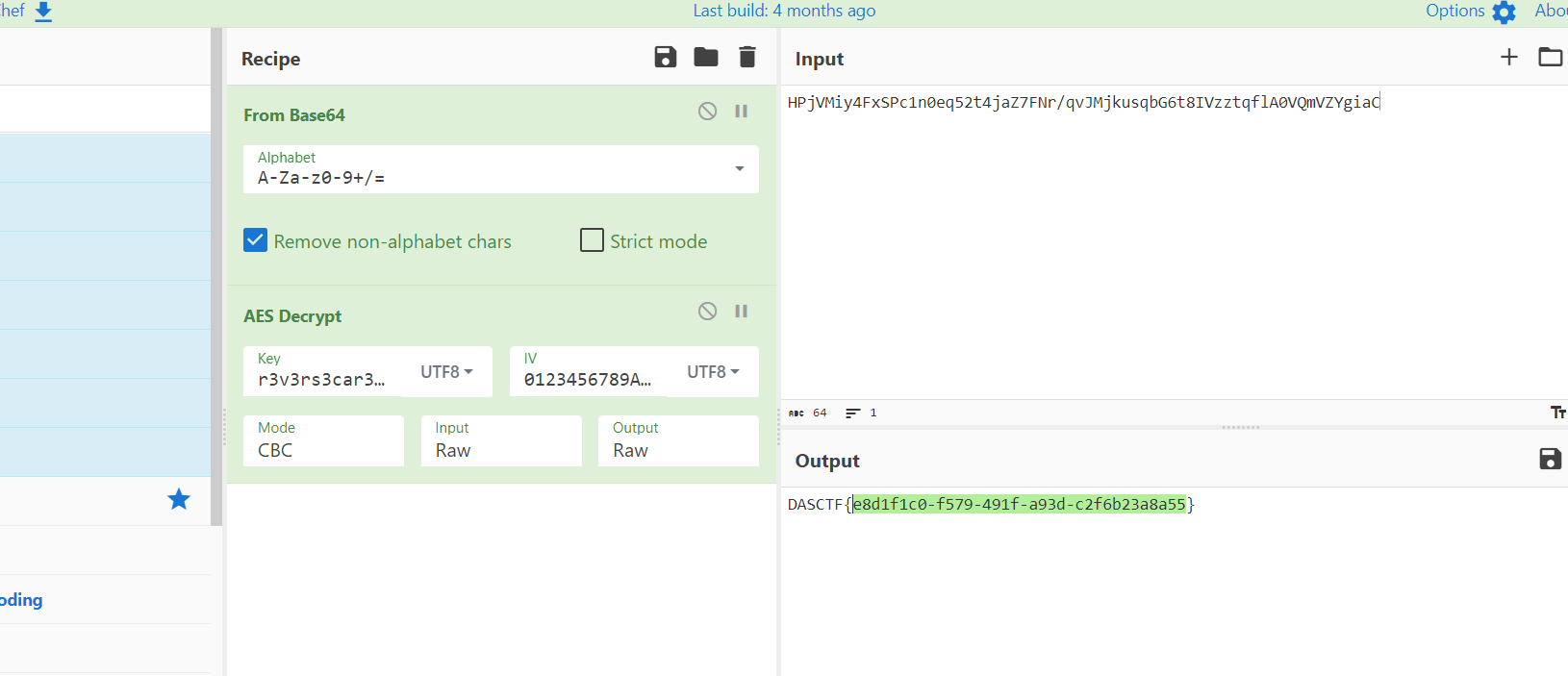
直接cyberchef
AndroidELF
魔改UPX,改回来就可以unpack
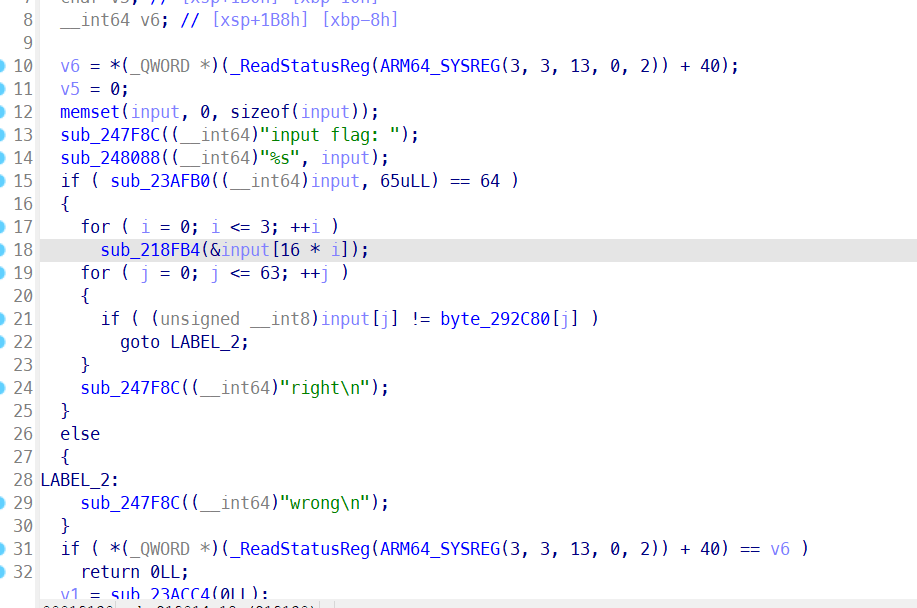
中间这个就是加密
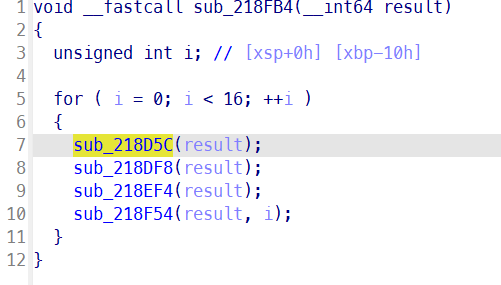
具体的不截图了,看脚本即可,分别对应四个函数的解密
from ctypes import c_uint8
enc = [0x3D, 0x45, 0x38, 0x7E, 0x78, 0x4B, 0x6A, 0x5C, 0x5B, 0x52, 0x4C, 0x73, 0x4E, 0x39, 0x49, 0x5F, 0x49, 0x40, 0x38, 0x5E, 0x74, 0x40, 0x66, 0x44, 0x46, 0x7A, 0x39, 0x3B, 0x67, 0x39, 0x70, 0x6C, 0x71, 0x5E, 0x6D, 0x4D, 0x5A, 0x4C, 0x7F, 0x3B, 0x4D, 0x63, 0x5E, 0x4E, 0x44, 0x5A, 0x7B, 0x51, 0x38, 0x61, 0x29, 0x63, 0x75, 0x5B, 0x67, 0x46, 0x4E, 0x5D, 0x79, 0x29, 0x4D, 0x29, 0x6D, 0x71]
table = [0x0000000D, 0x00000004, 0x00000000, 0x00000005, 0x00000002, 0x0000000C, 0x0000000B, 0x00000008, 0x0000000A, 0x00000006, 0x00000001, 0x00000009, 0x00000003, 0x0000000F, 0x00000007, 0x0000000E]
for j in reversed(range(4)):
for i in reversed(range(16)):
for i1 in range(16):
enc[i1+16*j]=c_uint8((120*i)^enc[i1+16*j]).value
for ii in reversed(range(16)):
enc[ii+16*j] = c_uint8(c_uint8(c_uint8(enc[ii+16*j]).value<<5).value | c_uint8(c_uint8(enc[ii+16*j]).value>>3).value).value
# print(enc)
temp = 16*[0]
for iii in range(16):
temp[iii] = enc[table[iii]+16*j]
for iij in range(16):
enc[iij+16*j] = temp[iij]
for iiii in range(16):
v1=0
for iiij in range(8):
v1 |= ((enc[16*j+iiii] >> iiij) & 1) << (7 - iiij)
enc[16*j+iiii] = v1
# break
# break
# break
print(''.join([chr(x) for x in enc]))